GRAY_HAT_927
SOCIAL ENGINEERING ATTACK
Social engineering is one of the most powerful ways to gain access to your target's information assets. Social engineering is a way to get someone to do something they wouldn't normally do for you, such as give you a private telephone number or internal confidential information, by creating a false trust relationship with them. It's no different from a common confidence game, also known as a "con" played by criminals the world over every day. You could even go as far as to say that the Greek's Trojan horse was an eraly act of social engineering.
The only thing that separates the gray hat hackers from a common criminal is ethical behaviour. Social enginnering attacks cover a wide range of activities, Phishing, for instance is a social engineering attak (SEA). The victims receive a legitimate-looking e-mail, follows a link to a legitimate-looking website they're familiar with, and often divulges sensitive information to a malicious third party. As end users are made aware of such activities, the attacks generally must become more sophisticated in order to remain effective. Recently, attacks of this nature have become narrowly targeted at specific companies, often mimicking internal system logins and targeting only individuals working at the subject company. It's an electronic numbers game conducted from afar, and the reason it is so common is that it works!
At the heart of every SEA is a human emotion, without which the attack will work. Emotion is what derails security policy and practices, by leading the human user to make an exception to the rules for what they believe is a good reason. Commonly exploited simple emotions and an example of how each is exploited:
- GREED A promise you'll get something very valuable if you do this one thing.
- LUST An offer to look at a sexy picture you just have to see.
- EMPATHY An appeal for help from someone impersonating someone you know.
- CURIOSITY Notice of something you just have to know, read or see.
- VANITY Isn't this a great picture of you?
These emotions are frequently used to get a computer user to perform a seemingly innocuous action, such as logging in to an online account or following an Internet URL from an e-mail or instant messaging client. The actual action is one of installing malicious software on their computer or divulging sensitive information.
Of course, there are more complex emotions exploited by more sophisticated social engineers. While sending someone an instant message with a link that says "Ilove this photo of you" is a straightforward appeal to their vanity, getting a secretary to fax youan internal contact list or a tech support agent to reset a password for you is quite a different matter. Attacks of this nature generally attempt to exploit more complex aspects of human bahaviour, such as:
- A DESIRE TO BE HELPFUL "if you're not busy, would you please copy this file from this CD to this USB flash drive for me?" most of us are taught from an early age to be friendly and helpful. We take this attitude with us to the workplace.
- AUTHORITY/CONFLICT AVOIDANCE "if you don't let me use the conference room to e-mail this report to Mr. Smith, it'll cost the company a lot of money and you your job" If the social engineering looks authoritative and unapproachable the target usually takes the easy way out by doing what's asked of them and avoiding a conflict.
- SOCIAL PROOF " hey look, my company has a FaceBook group and a lot of people I know have joined."If others are doing it, people feel more comfortable doing sonething they woudln't normally do alone.
No matter what emotional button the attacker is attemting to push, the premise is always the same: the intended victim will not sense the risk of their action or guess the real intentions of the attacker until it's too late or, in many cases, not at all. Because the intended victims in these cases most often are working on computers inside of the target company network, getting them to run a remote access program or otherwise grant you remote access directly or indirectly can be the fast tack to obtaining targeted sensitive data diring a penetration test.
Denail of Service Attack(DOS) and Distributed Denial of Service Attack(DDOS)
A denial-of-service attack overwhelms a system’s resources so that it cannot respond to service requests. A DDoS attack is also an attack on system’s resources, but it is launched from a large number of other host machines that are infected by malicious software controlled by the attacker.
Unlike attacks that are designed to enable the attacker to gain or increase access, denial-of-service doesn’t provide direct benefits for attackers. For some of them, it’s enough to have the satisfaction of service denial. However, if the attacked resource belongs to a business competitor, then the benefit to the attacker may be real enough. Another purpose of a DoS attack can be to take a system offline so that a different kind of attack can be launched. One common example is session hijacking, which I’ll describe later.
There are different types of DoS and DDoS attacks; the most common are TCP SYN flood attack, teardrop attack, smurf attack, ping-of-death attack and botnets.
TCP SYN flood attack
In this attack, an attacker exploits the use of the buffer space during a Transmission Control Protocol (TCP) session initialization handshake. The attacker’s device floods the target system’s small in-process queue with connection requests, but it does not respond when the target system replies to those requests. This causes the target system to time out while waiting for the response from the attacker’s device, which makes the system crash or become unusable when the connection queue fills up.
There are a few countermeasures to a TCP SYN flood attack:
- Place servers behind a firewall configured to stop inbound SYN packets.
- Increase the size of the connection queue and decrease the timeout on open connections.
Teardrop attack
This attack causes the length and fragmentation offset fields in sequential Internet Protocol (IP) packets to overlap one another on the attacked host; the attacked system attempts to reconstruct packets during the process but fails. The target system then becomes confused and crashes.
If users don’t have patches to protect against this DoS attack, disable SMBv2 and block ports 139 and 445.
Smurf attack
This attack involves using IP spoofing and the ICMP to saturate a target network with traffic. This attack method uses ICMP echo requests targeted at broadcast IP addresses. These ICMP requests originate from a spoofed “victim” address. For instance, if the intended victim address is 10.0.0.10, the attacker would spoof an ICMP echo request from 10.0.0.10 to the broadcast address 10.255.255.255. This request would go to all IPs in the range, with all the responses going back to 10.0.0.10, overwhelming the network. This process is repeatable, and can be automated to generate huge amounts of network congestion.
To protect your devices from this attack, you need to disable IP-directed broadcasts at the routers. This will prevent the ICMP echo broadcast request at the network devices. Another option would be to configure the end systems to keep them from responding to ICMP packets from broadcast addresses.
Ping of death attack
This type of attack uses IP packets to ‘ping a target system with an IP size over the maximum of 65,535 bytes. IP packets of this size are not allowed, so attacker fragments the IP packet. Once the target system reassembles the packet, it can experience buffer overflows and other crashes.
Ping of death attacks can be blocked by using a firewall that will check fragmented IP packets for maximum size.
Botnets
Botnets are the millions of systems infected with malware under hacker control in order to carry out DDoS attacks. These bots or zombie systems are used to carry out attacks against the target systems, often overwhelming the target system’s bandwidth and processing capabilities. These DDoS attacks are difficult to trace because botnets are located in differing geographic locations.
Botnets can be mitigated by:
- RFC3704 filtering, which will deny traffic from spoofed addresses and help ensure that traffic is traceable to its correct source network. For example, RFC3704 filtering will drop packets from bogon list addresses.
- Black hole filtering, which drops undesirable traffic before it enters a protected network. When a DDoS attack is detected, the BGP (Border Gateway Protocol) host should send routing updates to ISP routers so that they route all traffic heading to victim servers to a null0 interface at the next hop.
Man in the middle Attack
A MitM attacks also known as eavesdropping attacks, occurs when a hacker inserts itself between the communications of a client and a server. Here are some common types of man-in-the-middle attacks:
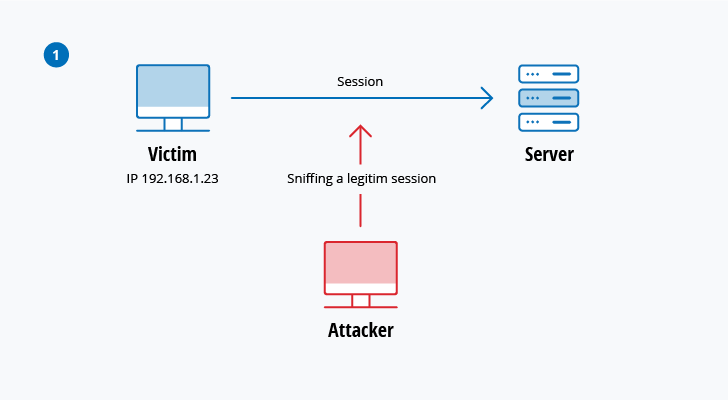
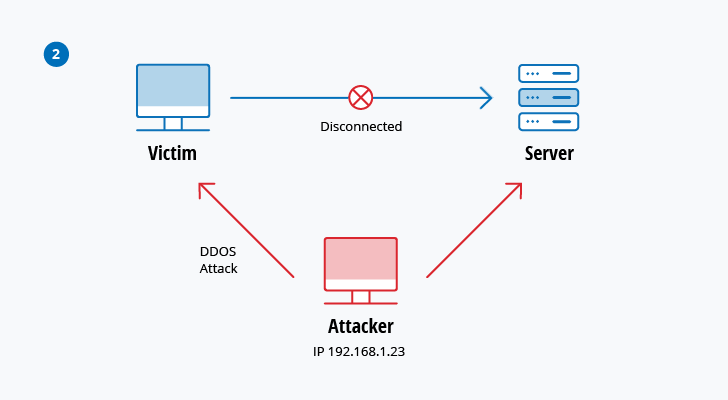
Session hijacking
In this type of MitM attack, an attacker hijacks a session between a trusted client and network server. The attacking computer substitutes its IP address for the trusted client while the server continues the session, believing it is communicating with the client. For instance, the attack might unfold like this:
- A client connects to a server.
- The attacker’s computer gains control of the client.
- The attacker’s computer disconnects the client from the server.
- The attacker’s computer replaces the client’s IP address with its own IP address and
spoofs the client’s sequence numbers. - The attacker’s computer continues dialog with the server and the server believes it is still communicating with the client.
IP Spoofing
IP spoofing is used by an attacker to convince a system that it is communicating with a known, trusted entity and provide the attacker with access to the system. The attacker sends a packet with the IP source address of a known, trusted host instead of its own IP source address to a target host. The target host might accept the packet and act upon it.
Replay
A replay attack occurs when an attacker intercepts and saves old messages and then tries to send them later, impersonating one of the participants. This type can be easily countered with session timestamps or nonce (a random number or a string that changes with time).
Currently, there is no single technology or configuration to prevent all MitM attacks. Generally, encryption and digital certificates provide an effective safeguard against MitM attacks, assuring both the confidentiality and integrity of communications. But a man-in-the-middle attack can be injected into the middle of communications in such a way that encryption will not help — for example, attacker “A” intercepts public key of person “P” and substitute it with his own public key. Then, anyone wanting to send an encrypted message to P using P’s public key is unknowingly using A’s public key. Therefore, A can read the message intended for P and then send the message to P, encrypted in P’s real public key, and P will never notice that the message was compromised. In addition, A could also modify the message before resending it to P. As you can see, P is using encryption and thinks that his information is protected but it is not, because of the MitM attack.
So, how can you make sure that P’s public key belongs to P and not to A? Certificate authorities and hash functions were created to solve this problem. When person 2 (P2) wants to send a message to P, and P wants to be sure that A will not read or modify the message and that the message actually came from P2, the following method must be used:
- P2 creates a symmetric key and encrypts it with P’s public key.
- P2 sends the encrypted symmetric key to P.
- P2 computes a hash function of the message and digitally signs it.
- P2 encrypts his message and the message’s signed hash using the symmetric key and sends the entire thing to P.
- P is able to receive the symmetric key from P2 because only he has the private key to decrypt the encryption.
- P, and only P, can decrypt the symmetrically encrypted message and signed hash because he has the symmetric key.
- He is able to verify that the message has not been altered because he can compute the hash of received message and compare it with digitally signed one.
- P is also able to prove to himself that P2 was the sender because only P2 can sign the hash so that it is verified with P2 public key.
Malware
Malicious software can be described as unwanted software that is installed in your system without your consent. It can attach itself to legitimate code and propagate; it can lurk in useful applications or replicate itself across the Internet. Here are some of the most common types of malware:
- Adware — Adware is a software application used by companies for marketing purposes; advertising banners are displayed while any program is running. Adware can be automatically downloaded to your system while browsing any website and can be viewed through pop-up windows or through a bar that appears on the computer screen automatically.
- Spyware — Spyware is a type of program that is installed to collect information about users, their computers or their browsing habits. It tracks everything you do without your knowledge and sends the data to a remote user. It also can download and install other malicious programs from the internet. Spyware works like adware but is usually a separate program that is installed unknowingly when you install another freeware application.
- Macro viruses — These viruses infect applications such as Microsoft Word or Excel. Macro viruses attach to an application’s initialization sequence. When the application is opened, the virus executes instructions before transferring control to the application. The virus replicates itself and attaches to other code in the computer system.
- File infectors — File infector viruses usually attach themselves to executable code, such as .exe files. The virus is installed when the code is loaded. Another version of a file infector associates itself with a file by creating a virus file with the same name, but an .exe extension. Therefore, when the file is opened, the virus code will execute.
- System or boot-record infectors — A boot-record virus attaches to the master boot record on hard disks. When the system is started, it will look at the boot sector and load the virus into memory, where it can propagate to other disks and computers.
- Polymorphic viruses — These viruses conceal themselves through varying cycles of encryption and decryption. The encrypted virus and an associated mutation engine are initially decrypted by a decryption program. The virus proceeds to infect an area of code. The mutation engine then develops a new decryption routine and the virus encrypts the mutation engine and a copy of the virus with an algorithm corresponding to the new decryption routine. The encrypted package of mutation engine and virus is attached to new code, and the process repeats. Such viruses are difficult to detect but have a high level of entropy because of the many modifications of their source code. Anti-virus software or free tools like Process Hacker can use this feature to detect them.
- Stealth viruses — Stealth viruses take over system functions to conceal themselves. They do this by compromising malware detection software so that the software will report an infected area as being uninfected. These viruses conceal any increase in the size of an infected file or changes to the file’s date and time of last modification.
- Trojans — A Trojan or a Trojan horse is a program that hides in a useful program and usually has a malicious function. A major difference between viruses and Trojans is that Trojans do not self-replicate. In addition to launching attacks on a system, a Trojan can establish a back door that can be exploited by attackers. For example, a Trojan can be programmed to open a high-numbered port so the hacker can use it to listen and then perform an attack.
- Logic bombs — A logic bomb is a type of malicious software that is appended to an application and is triggered by a specific occurrence, such as a logical condition or a specific date and time.
- Worms — Worms differ from viruses in that they do not attach to a host file, but are self-contained programs that propagate across networks and computers. Worms are commonly spread through email attachments; opening the attachment activates the worm program. A typical worm exploit involves the worm sending a copy of itself to every contact in an infected computer’s email address In addition to conducting malicious activities, a worm spreading across the internet and overloading email servers can result in denial-of-service attacks against nodes on the network.
- Droppers — A dropper is a program used to install viruses on computers. In many instances, the dropper is not infected with malicious code and, therefore might not be detected by virus-scanning software. A dropper can also connect to the internet and download updates to virus software that is resident on a compromised system.
- Ransomware — Ransomware is a type of malware that blocks access to the victim’s data and threatens to publish or delete it unless a ransom is paid. While some simple computer ransomware can lock the system in a way that is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called cryptoviral extortion, which encrypts the victim’s files in a way that makes them nearly impossible to recover without the decryption key.
Ransomware variants CryptoLocker, WannaCry, TeslaCrypt, Nyetya,Ryuk, Hermes.
RYUK Ransomeware
Similar to Samas an Bitpaymer,Ryuk is speacifically used to target entreprise environments, code comparison between versions of Ryuk and Hermes ransomeware indicate that Ryuk was derived from the Hermes source code en has been under steady development since its realease. Hermes is commodity ransomeware that has been observed for sale on forums and used by multiple threats actors. However, Ryuk is only used by GRIM SPIDER and unlike Hermes, Ryuk has only been used to target enterprise environments. Since Ryuk's appearance in August, the threat actors operating is have netted over 705.80 BTC across 52 transactions for a total current value of $3,701,893.98 USD.
The Ryuk ransom note is written to a file named RyukReadMe.txt A number of different ransom note templates have been observed. The body of the template is static with the exception of the email address and the Bitcoin (BTC) wallet address, wich may change. The email addresses usually contain one address at protonmail.com and another address at tutanota.com The email names typically are esoteric actors and directors, but Instagram models have also been observed. interestingly, the ransom note is remarkably similar to the BitPaymer ransome notes. As of this writing, it remains unclear if GIM SPIDER is copying the TTPs (tatics, techniques and procedures) and ransom notes or BitPaymer, or wether the groups may share information with each other. RYUK Ransomware
Phishing and Spear Phising Attacks
Phishing attack is the practice of sending emails that appear to be from trusted sources with the goal of gaining personal information or influencing users to do something. It combines social engineering and technical trickery. It could involve an attachment to an email that loads malware onto your computer. It could also be a link to an illegitimate website that can trick you into downloading malware or handing over your personal information.
Spear phishing is a very targeted type of phishing activity. Attackers take the time to conduct research into targets and create messages that are personal and relevant. Because of this, spear phishing can be very hard to identify and even harder to defend against. One of the simplest ways that a hacker can conduct a spear phishing attack is email spoofing, which is when the information in the “From” section of the email is falsified, making it appear as if it is coming from someone you know, such as your management or your partner company. Another technique that scammers use to add credibility to their story is website cloning — they copy legitimate websites to fool you into entering personally identifiable information (PII) or login credentials.
To reduce the risk of being phished, you can use these techniques:
- Critical thinking — Do not accept that an email is the real deal just because you’re busy or stressed or you have 150 other unread messages in your inbox. Stop for a minute and analyze the email.
- Hovering over the links — Move your mouse over the link, but do not click it! Just let your mouse cursor h over over the link and see where would actually take you. Apply critical thinking to decipher the URL.
- Analyzing email headers — Email headers define how an email got to your address. The “Reply-to” and “Return-Path” parameters should lead to the same domain as is stated in the email.
- Sandboxing — You can test email content in a sandbox environment, logging activity from opening the attachment or clicking the links inside the email.
SQL Injection
SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker).SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
SQL injection attacks allow attackers to spoof identity, tamper with existing data, cause repudiation issues such as voiding transactions or changing balances, allow the complete disclosure of all data on the system, destroy the data or make it otherwise unavailable, and become administrators of the database server.
In a 2012 study, it was observed that the average web application received 4 attack campaigns per month, and retailers received twice as many attacks as other industries.
History
The first public discussions of SQL injection started appearing around 1998; for example, a 1998 article in Phrack Magazine.
Form
SQL injection (SQLI) was considered one of the top 10 web application vulnerabilities of 2007 and 2010 by the Open Web Application Security Project. In 2013, SQLI was rated the number one attack on the OWASP top ten.There are four main sub-classes of SQL injection:
- Classic SQLI
- Blind or Inference SQL injection
- Data management system-specific SQLI
- Compounded SQLI
-
- SQL injection + insufficient authentication
- SQL injection + DDoS attacks
- SQL injection + DNS hijacking
- SQL injection + XSS
The Storm Worm is one representation of Compounded SQLI.
This classification represents the state of SQLI, respecting its evolution until 2010—further refinement is underway.
Technical implementations
Incorrectly filtered escape characters
This form of injection occurs when user input is not filtered for escape characters and is then passed into an SQL statement. This results in the potential manipulation of the statements performed on the database by the end-user of the application.
The following line of code illustrates this vulnerability:
statement = "SELECT * FROM users WHERE name = '" + userName + "';" This SQL code is designed to pull up the records of the specified username from its table of users. However, if the "userName" variable is crafted in a specific way by a malicious user, the SQL statement may do more than the code author intended. For example, setting the "userName" variable as:
' OR '1'='1 or using comments to even block the rest of the query (there are three types of SQL comments). All three lines have a space at the end:
' OR '1'='1' --
' OR '1'='1' {
' OR '1'='1' /* renders one of the following SQL statements by the parent language:
SELECT * FROM users WHERE name = '' OR '1'='1'; SELECT * FROM users WHERE name = '' OR '1'='1' -- '; If this code were to be used in an authentication procedure then this example could be used to force the selection of every data field (*) from all users rather than from one specific user name as the coder intended, because the evaluation of '1'='1' is always true.
The following value of "userName" in the statement below would cause the deletion of the "users" table as well as the selection of all data from the "userinfo" table (in essence revealing the information of every user), using an API that allows multiple statements:
a';DROP TABLE users; SELECT * FROM userinfo WHERE 't' = 't This input renders the final SQL statement as follows and specified:
SELECT * FROM users WHERE name = 'a';DROP TABLE users; SELECT * FROM userinfo WHERE 't' = 't';
While most SQL server implementations allow multiple statements to be executed with one call in this way, some SQL APIs such as PHP's mysql_query() function do not allow this for security reasons. This prevents attackers from injecting entirely separate queries, but doesn't stop them from modifying queries.
Blind SQL injection
Blind SQL injection is used when a web application is vulnerable to an SQL injection but the results of the injection are not visible to the attacker. The page with the vulnerability may not be one that displays data but will display differently depending on the results of a logical statement injected into the legitimate SQL statement called for that page. This type of attack has traditionally been considered time-intensive because a new statement needed to be crafted for each bit recovered, and depending on its structure, the attack may consist of many unsuccessful requests. Recent advancements have allowed each request to recover multiple bits, with no unsuccessful requests, allowing for more consistent and efficient extraction. There are several tools that can automate these attacks once the location of the vulnerability and the target information has been established.
Conditional responses
One type of blind SQL injection forces the database to evaluate a logical statement on an ordinary application screen. As an example, a book review website uses a query string to determine which book review to display. So the URLhttp://books.example.com/showReview.php?ID=5 would cause the server to run the query:
SELECT * FROM bookreviews WHERE ID = 'Value(ID)';
from which it would populate the review page with data from the review with ID 5, stored in the table bookreviews. The query happens completely on the server; the user does not know the names of the database, table, or fields, nor does the user know the query string. The user only sees that the above URL returns a book review. A hacker can load the URLs http://books.example.com/showReview.php?ID=5 OR 1=1http://books.example.com/showReview.php?ID=5 AND 1=2
SELECT * FROM bookreviews WHERE ID = '5' OR '1'='1';
SELECT * FROM bookreviews WHERE ID = '5' AND '1'='2';
respectively. If the original review loads with the "1=1" URL and a blank or error page is
returned from the "1=2" URL, and the returned page has not been created to alert the user the
input is invalid, or in other words, has been caught by an input test script, the site is likely vulnerable
to a SQL injection attack as the query will likely have passed through successfully in both cases.
The hacker may proceed with this query string designed to reveal the version number of MySQL
running on server: http://books.example.com/showReview.php?ID=5 AND substring
(@@version, 1, INSTR(@@version, '.')- 1)=4
a server running MySQL 4 and a blank or error page otherwise. The hacker can continue to use code
within query strings to achieve their goal directly, or to glean more information from the server in hopes
of discovering another avenue of attack.
Second order SQL injection
Second order SQL injection occurs when submitted values contain malicious commands that are stored rather than executed immediately. In some cases, the application may correctly encode an SQL statement and store it as valid SQL. Then, another part of that application without controls to protect against SQL injection might execute that stored SQL statement. This attack requires more knowledge of how submitted values are later used. Automated web application security scanners would not easily detect this type of SQL injection and may need to be manually instructed where to check for evidence that it is being attempted.
Mitigation
An SQL injection is a well known attack and easily prevented by simple measures. After an apparent SQL injection attack on TalkTalk in 2015, the BBC reported that security experts were stunned that such a large company would be vulnerable to it.
Detection
SQL injection filtering works in similar way to emails spam filters. Database firewalls detect SQL injections based on the number of invalid queries from host, while there are OR and UNION blocks inside of request, or others.
Parameterized statements
With most development platforms, parameterized statements that work with parameters can be used (sometimes called placeholders or bind variables) instead of embedding user input in the statement. A placeholder can only store a value of the given type and not an arbitrary SQL fragment. Hence the SQL injection would simply be treated as a strange (and probably invalid) parameter value. In many cases, the SQL statement is fixed, and each parameter is a scalar, not a table. The user input is then assigned (bound) to a parameter.
Easily put, using parameterized queries can definitely prevent SQL injection. This mainly means that your variables aren't query strings that would accept arbitrary SQL inputs, however, some parameters of given types are definitely necessary. Parameterized queries require the developer to define all the code. Therefore, without parameterized queries, anyone could put any kind of SQL code into the field, and have the database erased. But if the parameters were to set to '@username' then the person would only be able to put in a username without any kind of code.
Enforcement at the coding level
Using pbject-relational mapping libraries avoids the need to write SQL code. The ORM library in effect will generate parameterized SQL statements from object-oriented code.
Escaping
A straightforward, though error-prone way to prevent injections is to escape characters that have a special meaning in SQL. The manual for an SQL DBMS explains which characters have a special meaning, which allows creating a comprehensive blacklist of characters that need translation. For instance, every occurrence of a single quote (') in a parameter must be replaced by two single quotes ('') to form a valid SQL string literal. For example, in PHP it is usual to escape parameters using the function mysqli_real_escape_string(); before sending the SQL query:
$mysqli = new mysqli('hostname', 'db_username', 'db_password', 'db_name');
$query = sprintf("SELECT * FROM `Users` WHERE UserName='%s' AND Password='%s'",
$mysqli->real_escape_string($username),
$mysqli->real_escape_string($password));
$mysqli->query($query); This function prepends backslashes to the following characters: \x00, \n, \r, \, ', " and \x1a. This function is normally used to make data safe before sending a query to MySQL.
PHP has similar functions for other database systems such as pg_escape_string() for PostgreSQL. The function addslashes(string $str) works for escaping characters, and is used especially for querying on databases that do not have escaping functions in PHP. It returns a string with backslashes before characters that need to be quoted in database queries, etc. These characters are single quote ('), double quote ("), backslash (\) and NUL (the NULL byte).
Routinely passing escaped strings to SQL is error prone because it is easy to forget to escape a given string. Creating a transparent layer to secure the input can reduce this error-proneness, if not entirely eliminate it.
Pattern check
Integer, float or boolean, string parameters can be checked if their value is valid representation for the given type. Strings that must follow some strict pattern (date, UUID, alphanumeric only, etc.) can be checked if they match this pattern.
Database permissions
Limiting the permissions on the database login used by the web application to only what is needed may help reduce the effectiveness of any SQL injection attacks that exploit any bugs in the web application.
For example, on Microsoft SQL Server, a database logon could be restricted from selecting on some of the system tables which would limit exploits that try to insert JavaScript into all the text columns in the database.
deny select on sys.sysobjects to webdatabaselogon;
deny select on sys.objects to webdatabaselogon;
deny select on sys.tables to webdatabaselogon;
deny select on sys.views to webdatabaselogon;
deny select on sys.packages to webdatabaselogon;
Zero Day Exploit
A zero-day (also known as 0-day) vulnerability is a computer-software vulnerability that is unknown to, or unaddressed by, those who should be interested in mitigating the vulnerability (including the vendor of the target software). Until the vulnerability is mitigated, hackers can exploit it to adversely affect computer programs, data, additional computers or a network. An exploit directed at a zero-day is called a zero-day exploit, or zero-day attack.
In the jargon of computer security, "Day Zero" is the day on which the interested party (presumably the vendor of the targeted system) learns of the vulnerability, leading to the vulnerability being called a "zero-day". Once the vendor learns of the vulnerability, the vendor will usually create patches or advise workarouds to mitigate it.
The fewer the days since Day Zero, the higher the chance no fix or mitigation has been developed. Even after a fix is developed, the fewer the days since Day Zero, the higher is the probability that an attack against the afflicted software will be successful, because not every user of that software will have applied the fix. For zero-day exploits, unless the vulnerability is inadvertently fixed, e.g. by an unrelated update that happens to also obviate the need for a fix specific to the vulnerability, the probability that a user has applied a vendor-supplied patch that fixes the problem is zero, so the exploit would remain available. Zero-day attacks are a severe threat.
Attack vectors
Malware writers can exploit zero-day vulnerabilities through several different attack vectors. Sometimes, when users visit rogue websites, malicious code on the site can exploit vulnerabilities in Web browsers. Web browsers are a particular target for criminals because of their widespread distribution and usage. Cybercriminals, as well as international vendors of spyware such as Israel’s NSO group,can also send malicious e-mail attachments via SMTP, which exploit vulnerabilities in the application opening the attachment. Exploits that take advantage of common file types are numerous and frequent, as evidenced by their increasing appearances in databases like US-CERT. Criminals can engineer malware to take advantage of these file type exploits to compromise attacked systems or steal confidential data.
Window of vulnerability
The time from when a software exploit first becomes active to the time when the number of vulnerable systems shrinks to insignificance is known as the Window of Vulnerability (WoV). The time-line for each software vulnerability is defined by the following main events:
- t0 The vulnerability is discovered (by anyone).
- t1a A security patch is published (e.g., by the software vendor).
- t1b An exploit becomes active.
- t2 Most vulnerable systems have applied the patch.
Thus the formula for the length of the Window of Vulnerability is: t2 – t1b
In this formulation, it is always true that t0 ≤ t1a and t0 ≤ t1b. Note that t0 is not the same as Day Zero. For example, if a hacker is the first to discover (at t0) the vulnerability, the vendor might not learn of it until much later (on Day Zero).
For normal vulnerabilities, t1b – t1a > 0. This implies that the software vendor was aware of vulnerability and had time to publish a security patch (t1a) before any hacker could craft a workable exploit (t1b). For zero-day exploits, t1b – t1a ≤ 0 so that the exploit became active before a patch was made available.
By not disclosing known vulnerabilities, a software vendor hopes to reach t2 before t1b is reached, thus avoiding any exploits. However, the vendor has no guarantees that hackers will not find vulnerabilities on their own. Furthermore, hackers can analyze the security patches themselves, and thereby discover the underlying vulnerabilities and automatically generate working exploits. These exploits can be used effectively up until time t2.
In practice, the size of the WoV varies between systems, vendors, and individual vulnerabilities. It is often measured in days, with one report from 2006 estimating the average as 28 days.
Protection
Zero-day protection is the ability to provide protection against zero-day exploits. Since zero-day attacks are generally unknown to the public it is often difficult to defend against them. Zero-day attacks are often effective against "secure" networks and can remain undetected even after they are launched. Thus, users of so-called secure systems must also exercise common sense and practice safe computing habits.
Many techniques exist to limit the effectiveness of zero-day memory corruption vulnerabilities such as buffer overflows. These protection mechanisms exist in contemporary operating systems such as macOS, Windows Vista and beyond (see also: Security and safety features new to Windows Vista), Solaris, Linux, Unix, and Unix-like environments; Windows XP Service Pack 2 includes limited protection against generic memory corruption vulnerabilities and previous versions include even less. Desktop and server protection software also exists to mitigate zero-day buffer overflow vulnerabilities. Typically these technologies involve heurustic termination analysis—stopping them before they cause any harm.
It has been suggested that a solution of this kind may be out of reach because it is algorithmically impossible in the general case to analyze any arbitrary code to determine if it is malicious, as such an analysis reduces to the halting problem over a linear bounded automaton, which is unsolvable. It is, however, unnecessary to address the general case (that is, to sort all programs into the categories of malicious or non-malicious) under most circumstances in order to eliminate a wide range of malicious behaviors. It suffices to recognize the safety of a limited set of programs (e.g., those that can access or modify only a given subset of machine resources) while rejecting both some safe and all unsafe programs. This does require the integrity of those safe programs to be maintained, which may prove difficult in the face of a kernel level exploit.
The Zeroday Emergency Response Team (ZERT) was a group of software engineers who worked to release non-vendor patches for zero-day exploits.
Worms
Zero-day worms take advantage of a surprise attack while they are still unknown to computer security professionals. Recent history shows an increasing rate of worm propagation. Well designed worms can spread very fast with devastating consequences to the Internet and other systems.
Ethics
Differing ideologies exist relative to the collection and use of zero-day vulnerability information. Many computer security vendors perform research on zero-day vulnerabilities in order to better understand the nature of vulnerabilities and their exploitation by individuals, computer worms and viruses. Alternatively, some vendors purchase vulnerabilities to augment their research capacity. An example of such a program is TippingPoint's Zero Day Initiative. While selling and buying these vulnerabilities is not technically illegal in most parts of the world, there is a lot of controversy over the method of disclosure. A 2006 German decision to include Article 6 of the Convention on Cybercrime and the E U Framework Decision on Attacks agains Information System Decisitons may make selling or even manufacturing vulnerabilities illegal.
Most formal programs follow some form of Rain Forest Puppy's disclosure guidelines or the more recent OIS Guidelines for Security Vulnerability Reporting and Response. In general these rules forbid the public disclosure of vulnerabilities without notification to the vendor and adequate time to produce a patch.
Viruses
A zero-day virus (also known as zero-day malware or next-generation malware) is a previously unknown computer software or other malware for which specific antivirus software signatures are not yet available.
Traditionally, antivirus software relies upon signatures to identify malware. This can be very effective, but cannot defend against malware unless samples have already been obtained, signatures generated and updates distributed to users. Because of this, signature-based approaches are not effective against zero-day viruses.
Most modern antivirus software still uses signatures, but also carries out other types of analysis.
Code analysis
In code analysis, the machine code of the file is analysed to see if there is anything that looks suspicious. Typically, malware has characteristic behaviour and code analysis attempts to detect if this is present in the code.
Although useful, code analysis has significant limitations. It is not always easy to determine what a section of code is intended to do; particularly if it is very complex and has been deliberately written with the intention of defeating analysis. Another limitation of code analysis is the time and resources available. In the competitive world of antivirus software, there is always a balance between the effectiveness of analysis and the time delay involved.
Emulation
One approach to overcome the limitations of code analysis is for the antivirus software to run suspect sections of code in a safe sandbox and observe their behavior. This can be orders of magnitude faster than analyzing the same code, but must resist (and detect) attempts by the code to detect the sandbox.
Generic signatures
Generic signatures are signatures that are specific to certain behaviour rather than a specific item of malware. Most new malware is not totally novel, but is a variation on earlier malware, or contains code from one or more earlier examples of malware. Thus the results of previous analysis can be used against new malware.
Competitiveness in the antivirus software industry
It is generally accepted in the antivirus industry that most vendors' signature-based protection is identically effective. If a signature is available for an item of malware, then every product (unless dysfunctional) should detect it. However, some vendors are significantly faster than others at becoming aware of new viruses and/or updating their customers' signature databases to detect them.
There is a wide range of effectiveness in terms of zero-day virus protection. The German computer magazine c't found that detection rates for zero-day viruses varied from 20% to 68%.It is primarily in the area of zero-day virus performance that manufacturers now compete.
U.S. government involvement
NSA's use of zero-day exploits (2017)
In mid-April 2017 the hackers known as The Shadow Brokers (TSB)—allegedly linked to the Russian governmenT—released files from the NSA (initially just regarded as alleged to be from the NSA, later confirmed through internal details and by Snowden)which include a series of 'zero-day exploits' targeting Microsoft Windows software and a tool to penetrate the Society for Worldwide Interbank Financial Telecommunication(SWIFT)'s service provider.Ars Technica had reported Shadow Brokers' hacking claims in mid-January 2017 and in April the Shadow Brokers posted the exploits as proof.
Vulnerabilities Equities Process
The Vulnrabilities Equities Process, first revealed publicly in 2016, is a process used by the U.S. fedral govermment to determine on a case-by-case basis how it should treat zero-day. computer security vulnerabilities; whether to disclose them to the public to help improve general computer security, or to keep them secret for offensive use against the government's adversaries.
The process has been criticized for a number of deficiencies, including restriction by non-disclosure agreements, lack of risk ratings, special treatment for the NSA, and less than whole-hearted commitment to disclosure as the default option.
Signature-based detection
A virus signature is a unique pattern or code that can be used to detect and identify specific viruses. The antivirus scans file signatures and compares them to a database of known malicious codes. If they match, the file is flagged and treated as a threat. The major limitation of signature-based detection is that it is only capable of flagging already known malware, making it completely useless against zero-day attacks.